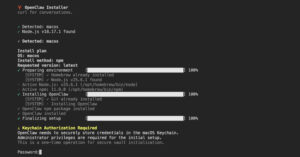
Threat Actors Mass-Scan Salesforce Experience Cloud via Modified AuraInspector Tool
Salesforce has warned of an increase in threat actor activity that’s aimed at exploiting misconfigurations in publicly accessible Experience Cloud sites by making use of