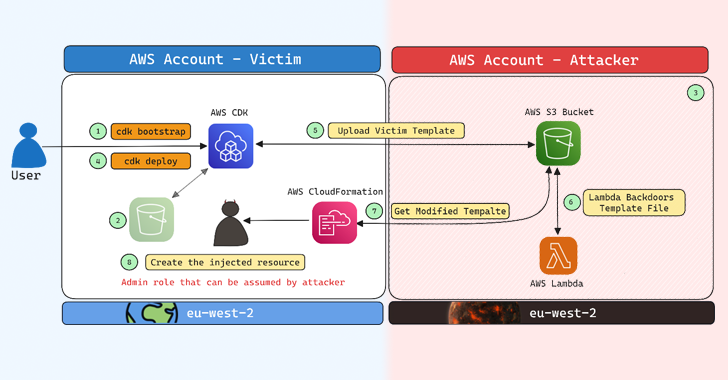
New Qilin.B Ransomware Variant Emerges with Improved Encryption and Evasion Tactics
Cybersecurity researchers have discovered an advanced version of the Qilin ransomware sporting increased sophistication and tactics to evade detection. The new variant is being tracked by cybersecurity firm Halcyon under the moniker Qilin.B. “Notably, Qilin.B now supports AES-256-CTR encryption for