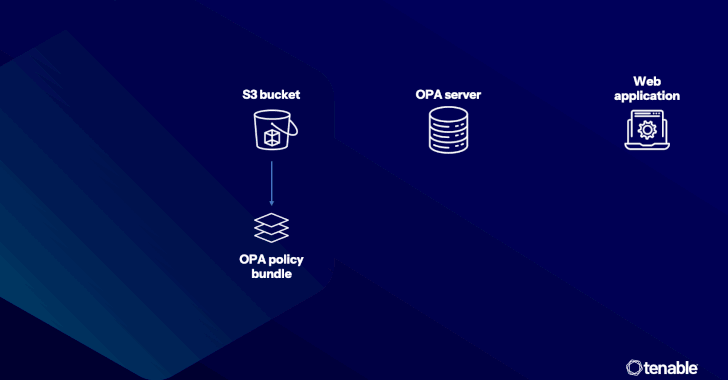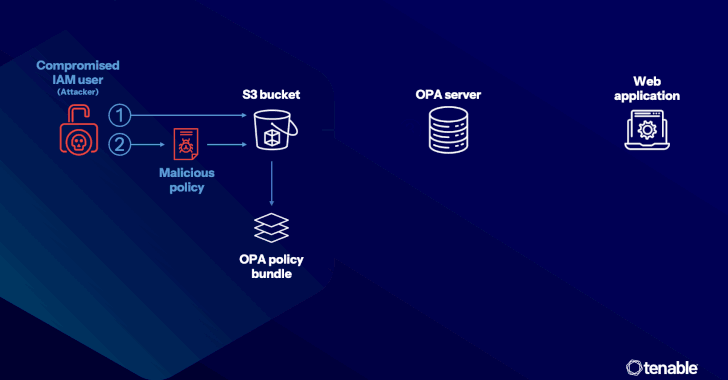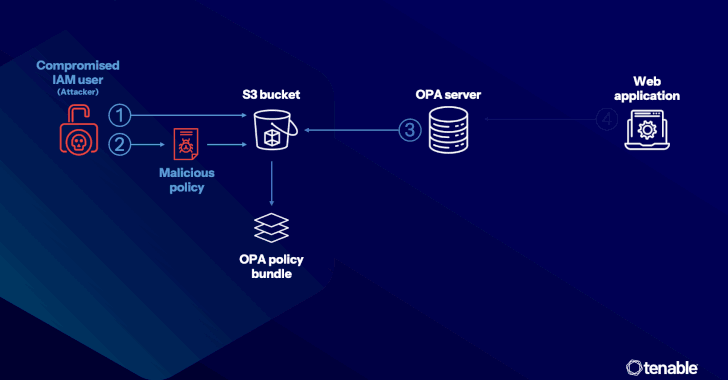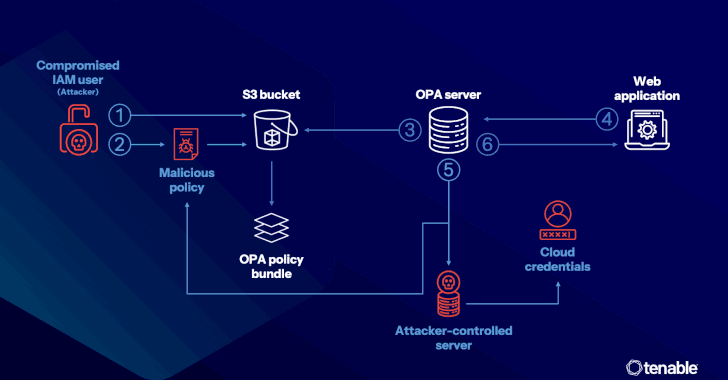
Google’s New Restore Credentials Tool Simplifies App Login After Android Migration
Google has introduced a new feature called Restore Credentials to help users restore their account access to third-party apps securely after migrating to a new Android device. Part of Android’s Credential Manager API, the feature aims to reduce the hassle