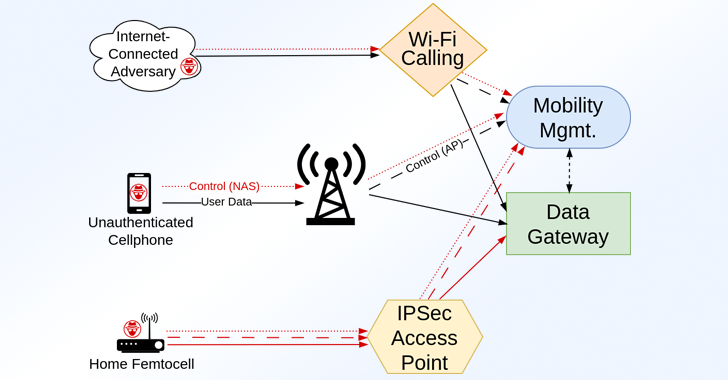
RANsacked: Over 100 Security Flaws Found in LTE and 5G Network Implementations
A group of academics has disclosed details of over 100 security vulnerabilities impacting LTE and 5G implementations that could be exploited by an attacker to disrupt access to service and even gain a foothold into the cellular core network. The