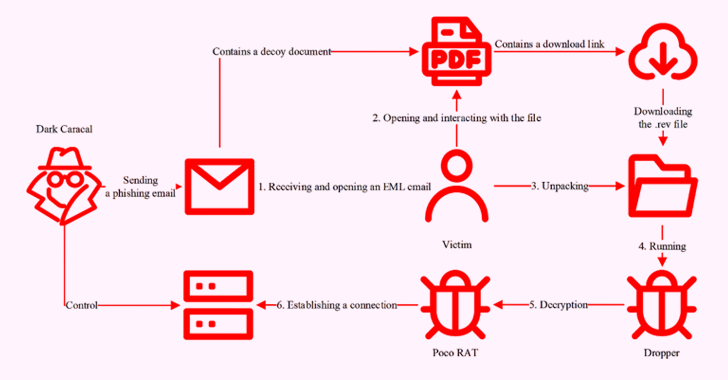
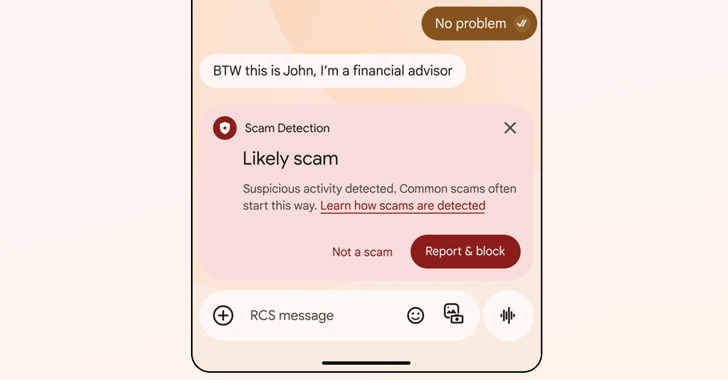
China-Linked Silk Typhoon Expands Cyber Attacks to IT Supply Chains for Initial Access
The China-lined threat actor behind the zero-day exploitation of security flaws in Microsoft Exchange servers in January 2021 has shifted its tactics to target the information technology (IT) supply chain as a means to obtain initial access to corporate networks.