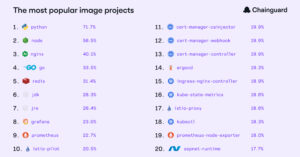
WhatsApp Worm Spreads Astaroth Banking Trojan Across Brazil via Contact Auto-Messaging
Cybersecurity researchers have disclosed details of a new campaign that uses WhatsApp as a distribution vector for a Windows banking trojan called Astaroth in attacks