



Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks
1 minute read
Uncategorized
Updated on February 18, 2025

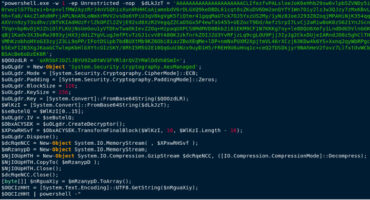
The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing a novel technique to evade detection and maintain control over infected systems.
This involves the use of a legitimate Microsoft Windows utility called Microsoft Application Virtualization Injector (MAVInject.exe) to inject the threat actor’s malicious payload into an external process, waitfor.exe,…
Read the rest of the story at Read More
Source: The Hacker News













Leave a Comment