



New Sni5Gect Attack Crashes Phones and Downgrades 5G to 4G without Rogue Base Station
1 minute read
Uncategorized
Updated on August 26, 2025
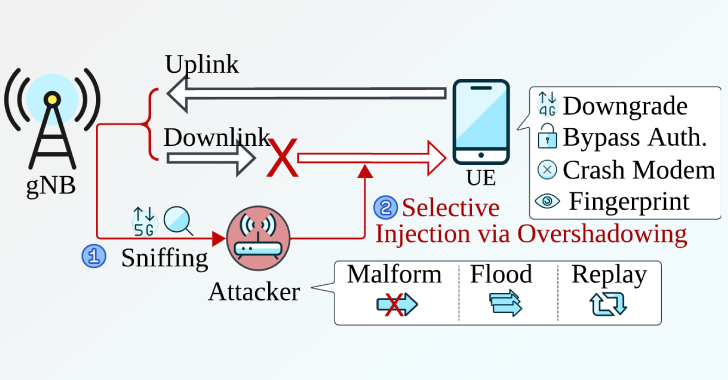
A team of academics has devised a novel attack that can be used to downgrade a 5G connection to a lower generation without relying on a rogue base station (gNB).
The attack, per the ASSET (Automated Systems SEcuriTy) Research Group at the Singapore University of Technology and Design (SUTD), relies on a new open-source software toolkit named Sni5Gect (short for “Sniffing 5G Inject”) that’s…
Read the rest of the story at Read More
Source: The Hacker News














Leave a Comment