



Orchid Security Introduces Continuous Identity Observability for Enterprise Applications
1 minute read
Uncategorized
Updated on February 4, 2026
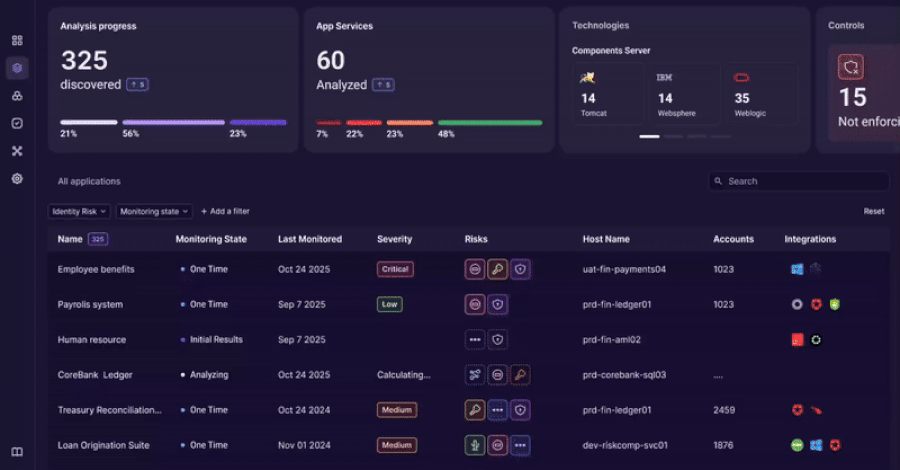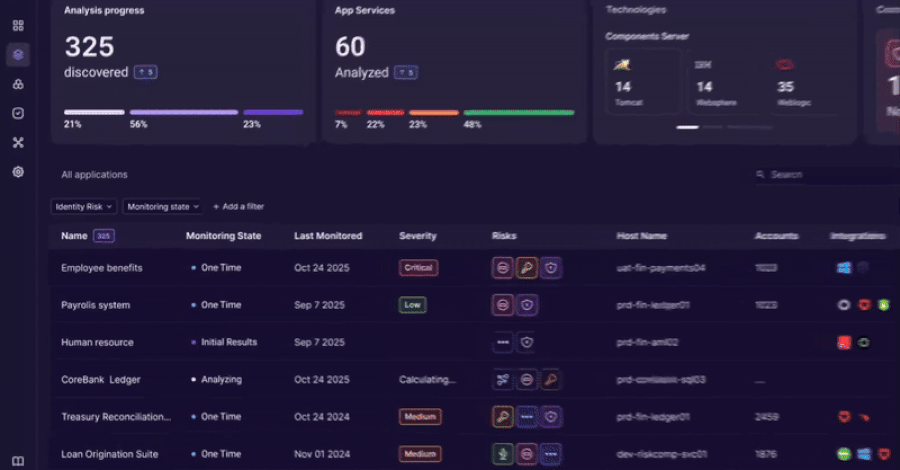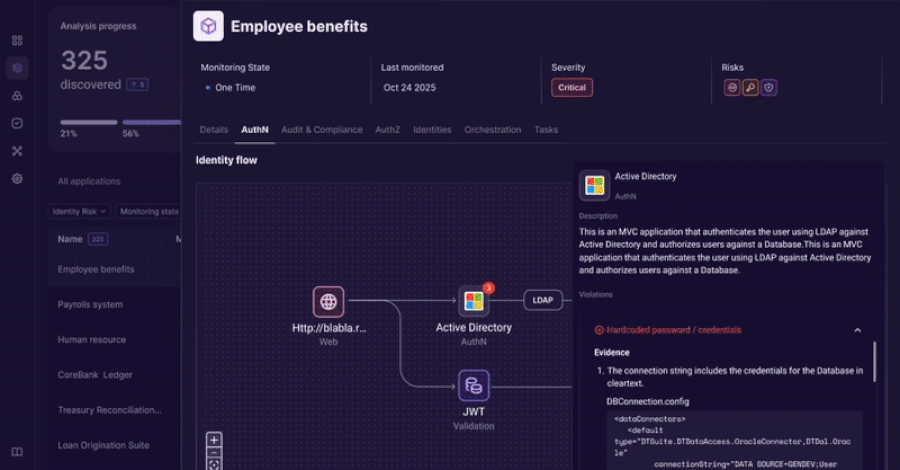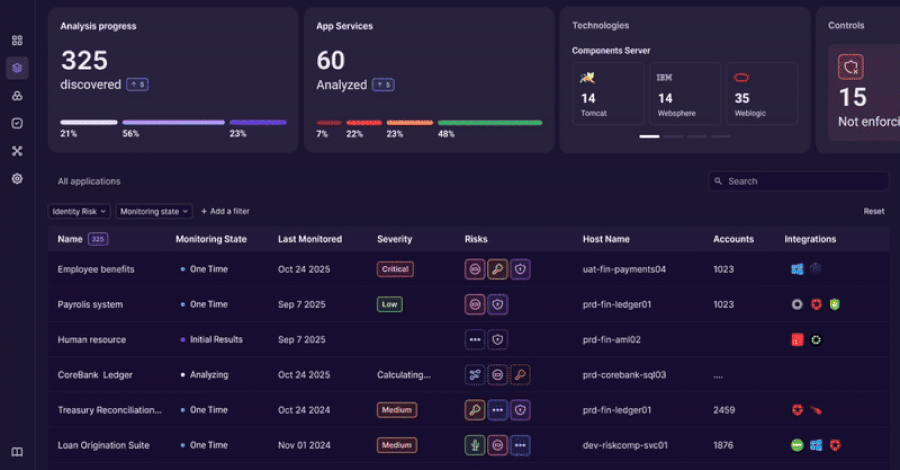
An innovative approach to discovering, analyzing, and governing identity usage beyond traditional IAM controls.
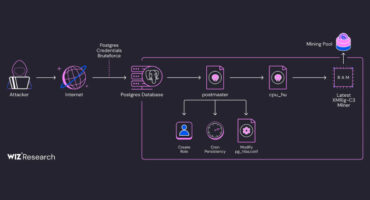
The Challenge: Identity Lives Outside the Identity Stack
Identity and access management tools were built to govern users and directories.
Modern enterprises run on applications. Over time, identity logic has moved into application code, APIs, service accounts, and custom authentication…
Read the rest of the story at Read More
Source: The Hacker News












Leave a Comment