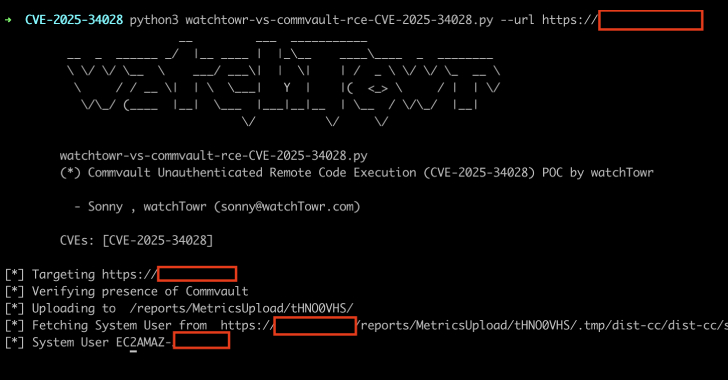
Critical Commvault Command Center Flaw Enables Attackers to Execute Code Remotely
A critical security flaw has been disclosed in the Commvault Command Center that could allow arbitrary code execution on affected installations. The vulnerability, tracked as CVE-2025-34028, carries a CVSS score of 9.0 out of a maximum of 10.0. “A critical