



GootLoader Malware Uses 500–1,000 Concatenated ZIP Archives to Evade Detection
1 minute read
Uncategorized
Updated on January 16, 2026
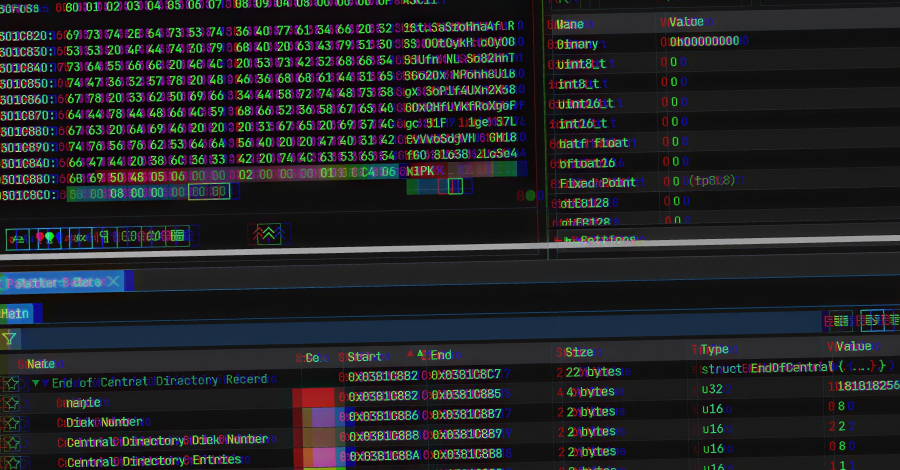
The JavaScript (aka JScript) malware loader called GootLoader has been observed using a malformed ZIP archive that’s designed to sidestep detection efforts by concatenating anywhere from 500 to 1,000 archives.
“The actor creates a malformed archive as an anti-analysis technique,” Expel security researcher Aaron Walton said in a report shared with The Hacker News. “That is, many unarchiving tools…
Read the rest of the story at Read More
Source: The Hacker News












Leave a Comment