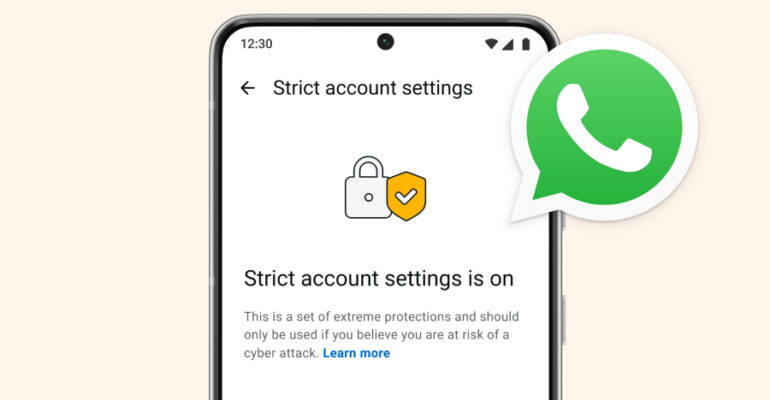
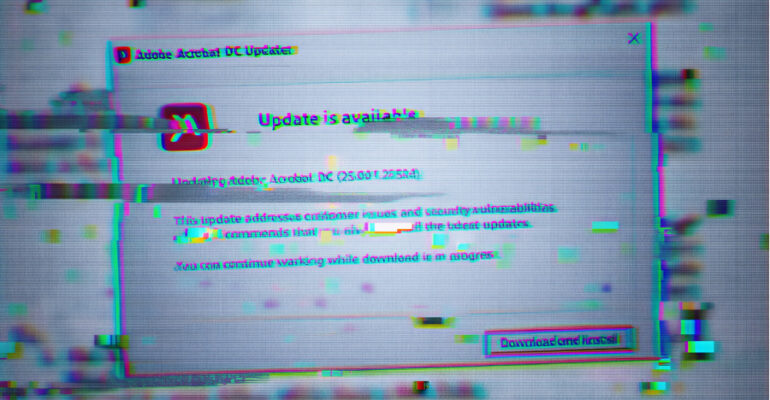
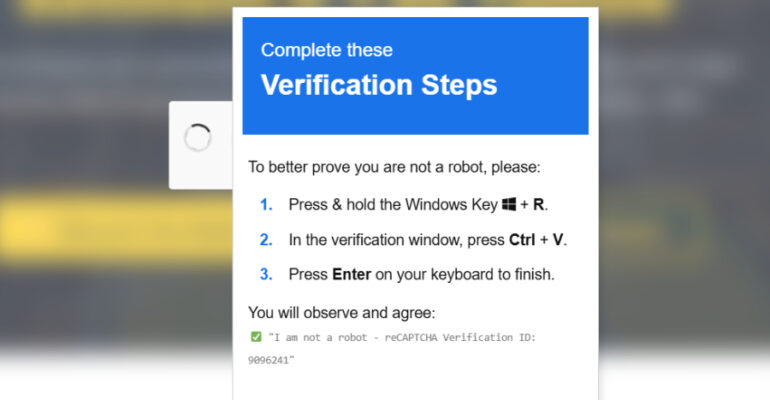
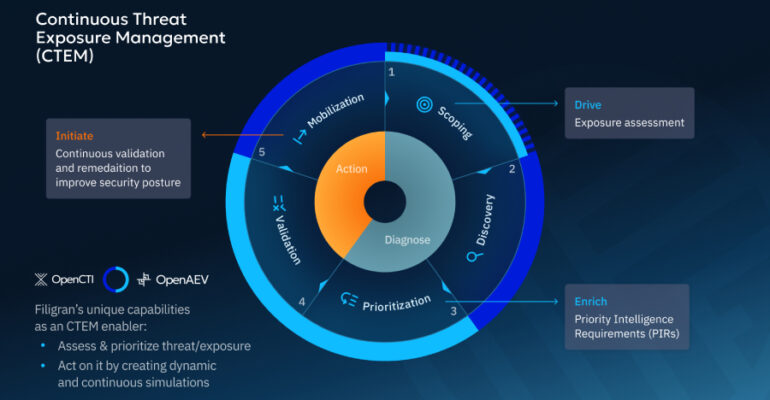
Google Warns of Active Exploitation of WinRAR Vulnerability CVE-2025-8088
Google on Tuesday revealed that multiple threat actors, including nation-state adversaries and financially motivated groups, are exploiting a now-patched critical security flaw in RARLAB WinRAR to establish initial access and deploy a diverse array of payloads. “Discovered and patched in